Release highlights
This release includes our new local code analysis agent which is an exciting announcement!
New local code analysis agent – run our code intelligence analysis on your own machine!
This is something we’ve been working on for a while, the ability to run a simple command on your local machine or server, analyse your code using the same code intelligence engine as our SaaS platform and view the results in our normal web interface, the same as any other code vault.
Previously the only ways to analyse your code were to sync it from your GIT repository, or give our platform the URL to a file archive hosted somewhere such as Google Drive, Dropbox, One Drive etc.
This still caused some issues with companies with strict code policies or just customers that didn’t like the idea of someone else syncing the code (even though we have documented the security of our infrastructure :).
So we knew that we had provide another option.
At first we thought it wouldn’t be possible due to the way our code analysis engine is architecture – it runs on various microservices, with separation of concerns and each one doing it’s own analysis in it’s own way, independent of all other services.
But we’re excited to announce that our very clever engineering team came up with a way to package this all into a single command that anyone can run from their own machine (or their developer’s machine, or a server!).
As the command is docker-based, it should run on Windows, Macs and Linux machines!
This is what it does:
- Downloads the latest Docker container image with our analysis engine on it
- Analyses the code in the current folder, or another folder you give it
- Creates a local anonymous .zip file of the analysis findings, which doesn’t contain your source code
- It does however contain minimal code snippets (sometimes a single line) for detected security vulnerabilities, to show you where it was detected.
- Uploads the .zip file to our secure encrypted file store, and tells our platform it’s ready
- Our platform then simply extracts the .zip file, inserts the data into your code vault, and it’s ready for you to view!
- Your .zip file is then deleted from our file store as soon as it’s processed.
There are a few caveats:
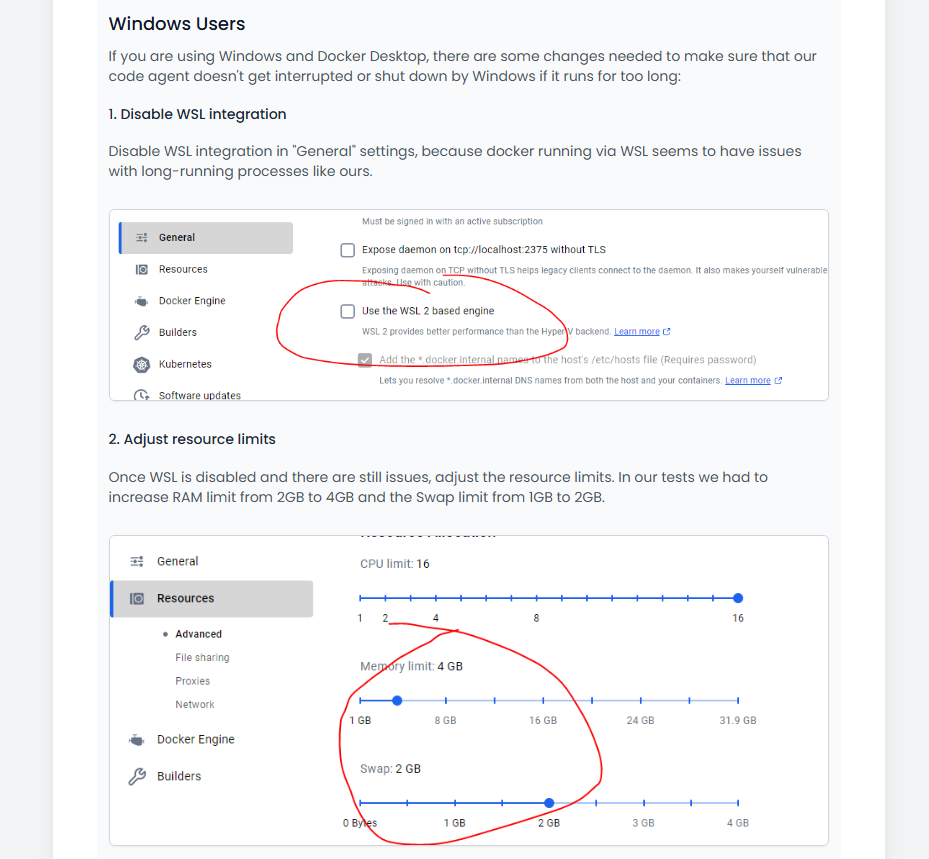
For Windows users there are sometimes issues with long running, memory intensive processes running via Docker. We’ve added some additional setup steps to try and avoid these in the instructions (see below).
If there is a .git folder (i.e. the folder being analysed is a cloned GIT repository), the code agent will analyse the GIT history and branches as well. You can stop that by simply removing (or temporarily moving) the .git folder.
When analysing the .git folder, it will only analyse what you have checked out. For example you may have only worked on a few branches, so your .git folder won’t have the full history and all branches to be analysed. You can run this command on your folder to make sure it has ALL GIT history and data to be analysed by our agent: “git fetch –all”
If you want to simply generate the .zip file without sending to us yet, so you can see what it contains, simply run the command with –dry-run at the end. This will create the .zip file and not go any further. Once you’re happy with the contents, delete the .zip file (it’s normally left on your machine for your own records) and run the command again without –dry-run.
And here’s how it looks!
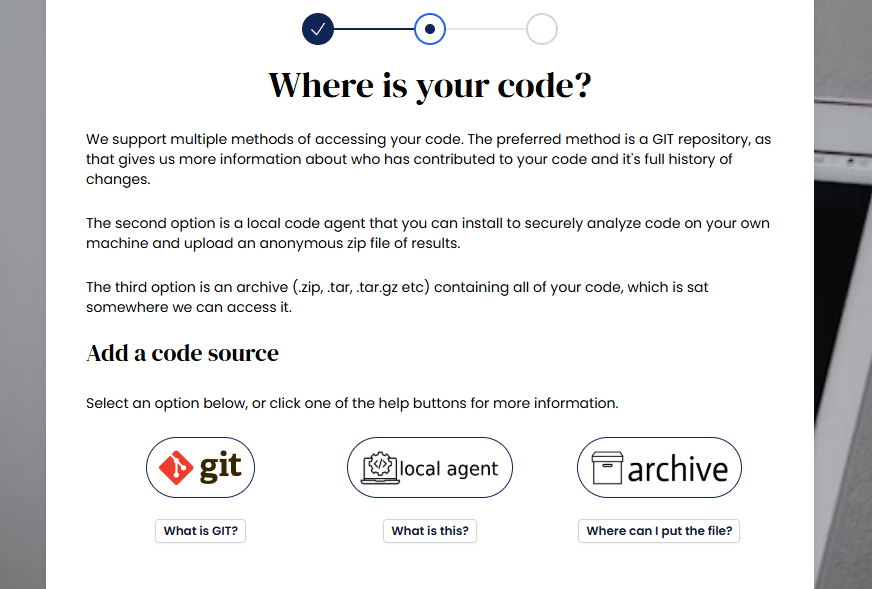
New local code agent option when creating a project:
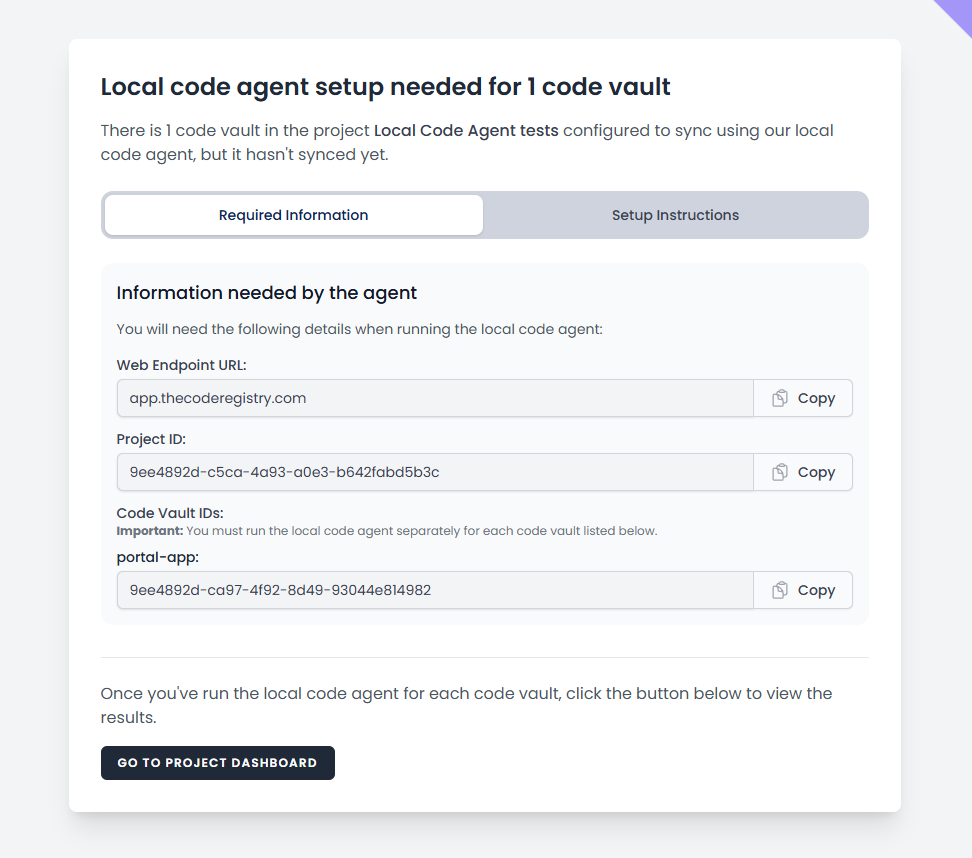
The local code agent instructions you are shown after creating the project:
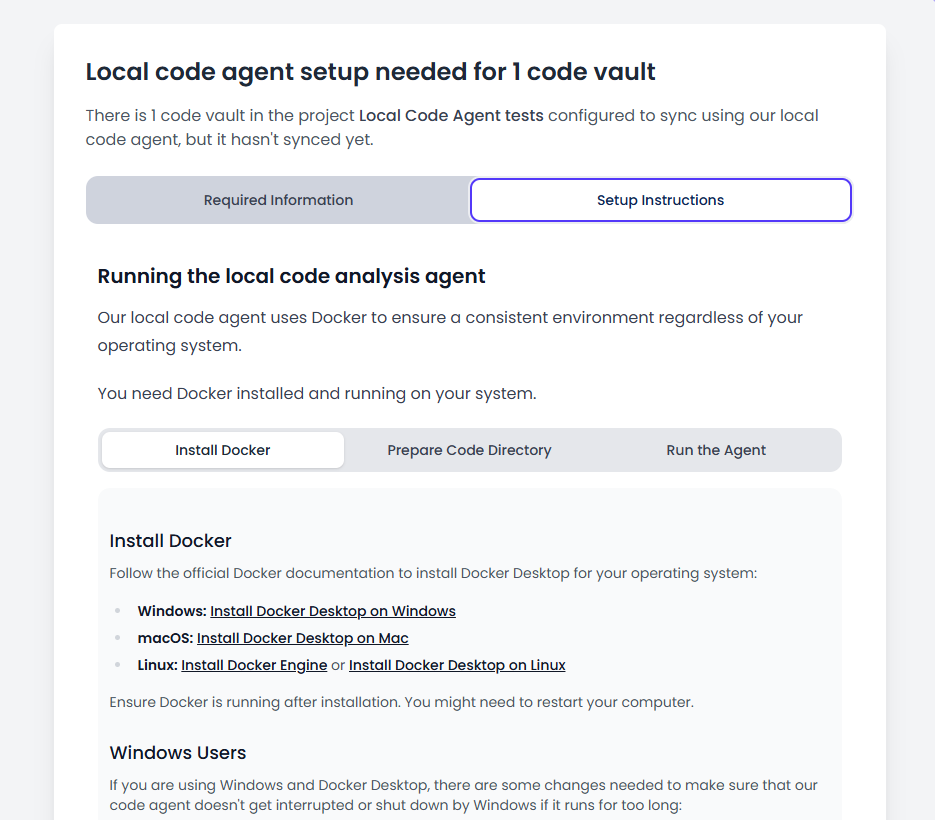
Instructions showing the command to run:
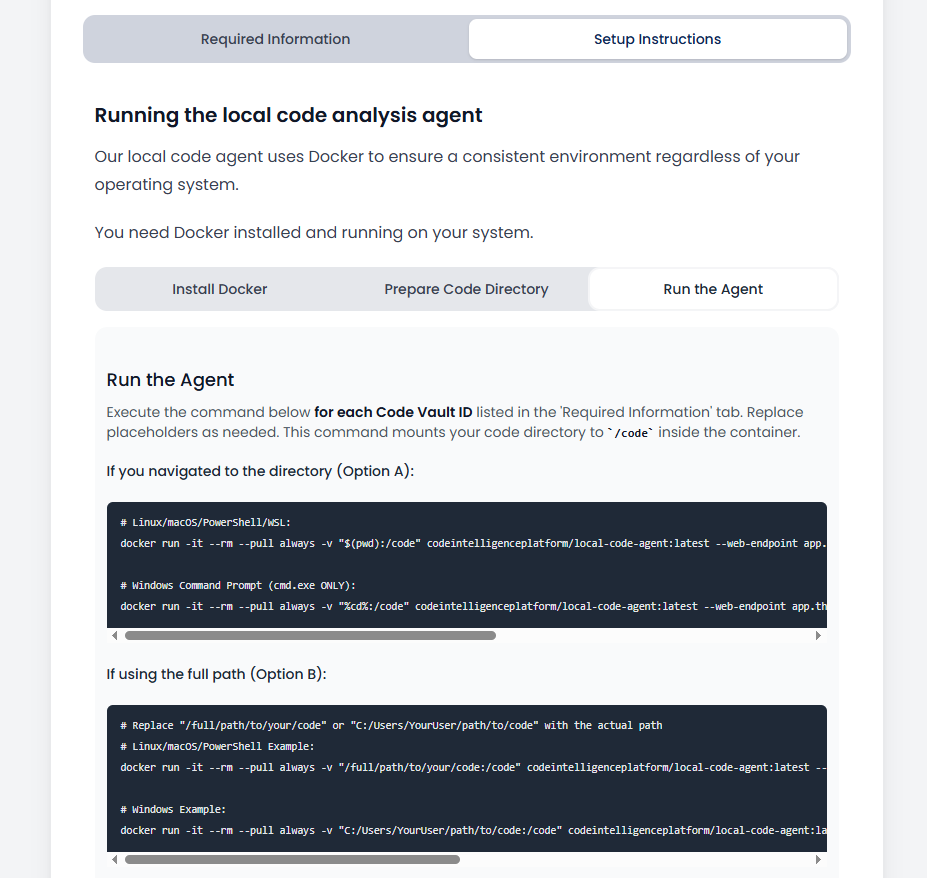
Windows-specific instructions in case of any issues:
Example output from our local code agent:

Please note: As this is a big new development, please let us know of any issues and we’ll jump right on it!
Other changes
Big improvement to page performance when viewing security issues
This has been coming up a few times in our own testing – page speed issues when browsing security issues. We’ve essentially rewritten most of this functionality and now it is a LOT quicker!
Improved auto-retry mechanism when file type / language analysis has issues
We noticed some edge cases where the file type / language analysis failed and returned the wrong number of file types or languages. This then had a knock-on effect in some other areas like the cost-to-replicate analysis.
We’ve improved this error detection and retry mechanism to make sure this analysis is re-run automatically in these cases.
Improved error handling for odd Azure filesystem errors in the security analyser
We noticed there are sometimes – very rarely – some odd Azure filesystem errors in the security analyser. For example it can’t find files or folders. We’ve added some workarounds and retry mechanisms for this.
The joys of serverless scalable functions in the cloud!
Improved messaging around selecting GIT branches
Added a bit of wording to make it clear why a user may want to specify a GIT branch when adding a project/code vault.
Bug fixes
Fixed a bug in the GitLab integration where not all repositories were loaded, due to API limitations
Fixed a bug where in some cases the number of projects left on your account was calculated wrong
Fixed a bug where some free escrow certificate features didn’t show in some circumstances
- Fixed a bug where too much data was sent to the AI layer to generate security issue summaries, causing an error due to context limits
- Fixed a bug where a user’s current team is deleted, and they get an error when logging in (because their current team no longer exists).
- Fixed a broken link to create an account inside the team member invitation email. This was due to a change with our Authentication service provider recently.
- Fixed a bug with odd symbols in AIQ issues contents causing errors.
- Fixed a bug in the developer productivity where if all scores in the yearly output trend for a specific developer were 100, the chart didn’t show correctly
Want to Learn More?




